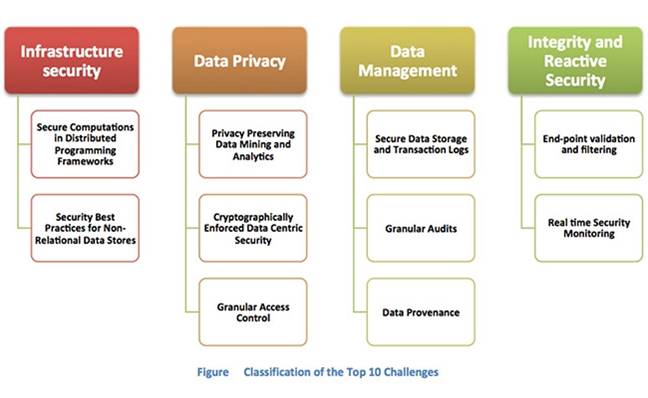
Security is always highly emphasized in ‘Oasis Inventor’. Here 3 aspects of security measures are usually performed – namely Physical Security, Workflow Security and Data Security; to secure the confidentiality and integrity of customer information.
Physical Security:
- The office premises are secured using smart card and access lock; through which all access in and out is controlled.
- Log book for each visitor at the main entrance level and visitor badge shall
 be wear all times during office visit.
be wear all times during office visit. - CCTV has been installed to keep track of the operational activities.
- Regular management review is carried out always.
- No personal belongings are allowed to be brought into the operation rooms.
- High level of confidentiality incurred against all sorts of documents/images being processed.
Workflow Security:
Workflows are controlled as per ISO requirements in order to offer the highest security and integrity to customer’s assets.
Data Security:
In order to offer best possible protection against customer’s data; 5 different levels of security measurements have been applied during the process of transmission, storage and processing.
- Centre Protection: – Firewalls along with the features like VPN, intrusion protection as well as NAT/PAT support are set up in our data centre to prevent any illegal access from outsides.
- Data Storage: – All customer data reside in the server will remain encrypted until the data is processed. Decryption will be done through application.
- Access Control: – User ID and password will be used for every application. Only authorized operators can access the application as well as customer’s data.
- Audit trail report: – Complete log report will be generated to monitor every transaction made during processing; ensuring customer’s data is handled properly.
- File Eraser: – Processed files upon transmission will be erased using the software File Eraser to ensure that no data recovery can be made illegally.